*Introduction ;-
Telnet is a application protocol used on the internet or local area network . it is provided in to a bidirectional interactive text oriented communication facility using a virtual terminal connection.
Telnet was developed in 1969.
Historically, Telnet provided access to a command-line interface on a remote host.Telnet is also
used to refer to the software that implements the clients part of the protocol. Telnet client application are available for virtually all computer platforms. Telnet means Telecommunication network.
Telecommunication Network ;-
A telecommunication network is a group of nodes interconnected by links that are used to exchange messages between the nodes. The links may use a variety of technologies based on the methodologies of circuit switching, message switching, or packet switching, to pass messages and signals.
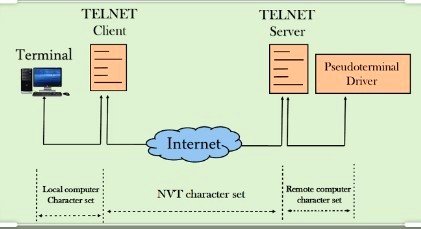
>One computer give permission to other computer is called Remote Login.
>We connect with Remote computer or Host computer .
>We use Unix command in CUI (command -line interface).
>We use Unix based Email program that is called PINE (email client)
Establish telnet connection :-
Procedure;->
First open to telnet-> Telnet option -> Enter computer name and IP address.
1.After you can configure router.
2.You can read email of remote computer.
3.We use which software with talent that is called VT100.
4.We use which keyboard with telnet that is called NVT (Network virtual terminal) keyboard.
5.we use which printer with telnet that is called NVT virtual printer.
*SECURITY;-
When Telnet was developed in 1969, most users of networked computers were in the computer departments of academic institutions , or at large private and Government research facilities.
In this environment, security was not nearly as much a concern as it became after the bandwidth
explosion of the 1990S. The rise in the number of people with access to the internet, and by extension
the number of people attempting to hack other peoples servers, made encrypted alternatives necessary.
Most implementations of Telnet have no authentication that would ensure communication is carried out between the two desired hosts and not intercepted in the middle.
Several vulnerabilities have been discovered over the years in commonly used Telnet.
*Telnet 5250;-
IBM 5250 or 3270 workstation emulation is supported via custom telnet clients, TN 5250/ TN 3270
and IBM servers. Clients and Servers designed to pass IBM 5250 data streams over Telnet generally do support SSL encryption, as SSH does not include 5250 emulation. Under OS/400, Port 992 is the default port for secured telnet.
LATEST TELNET CONNECTION APPLICATION SOFTWARE NAME;-
1. Team Viewer
2. Any desk
CLICK THIS IMAGE DIRECT GO TO THE APPLICATION SITE